Your Mainframe is Secure, Your Security Practice is Not
It's the holidays again! But before you settle down with some eggnog and carols, let's talk about something a little less festive: mainframe security.
Just like Santa keeps a watchful eye on who's been naughty or nice, hackers are always looking for weaknesses to exploit. And unfortunately, many organizations are making it too easy for them.
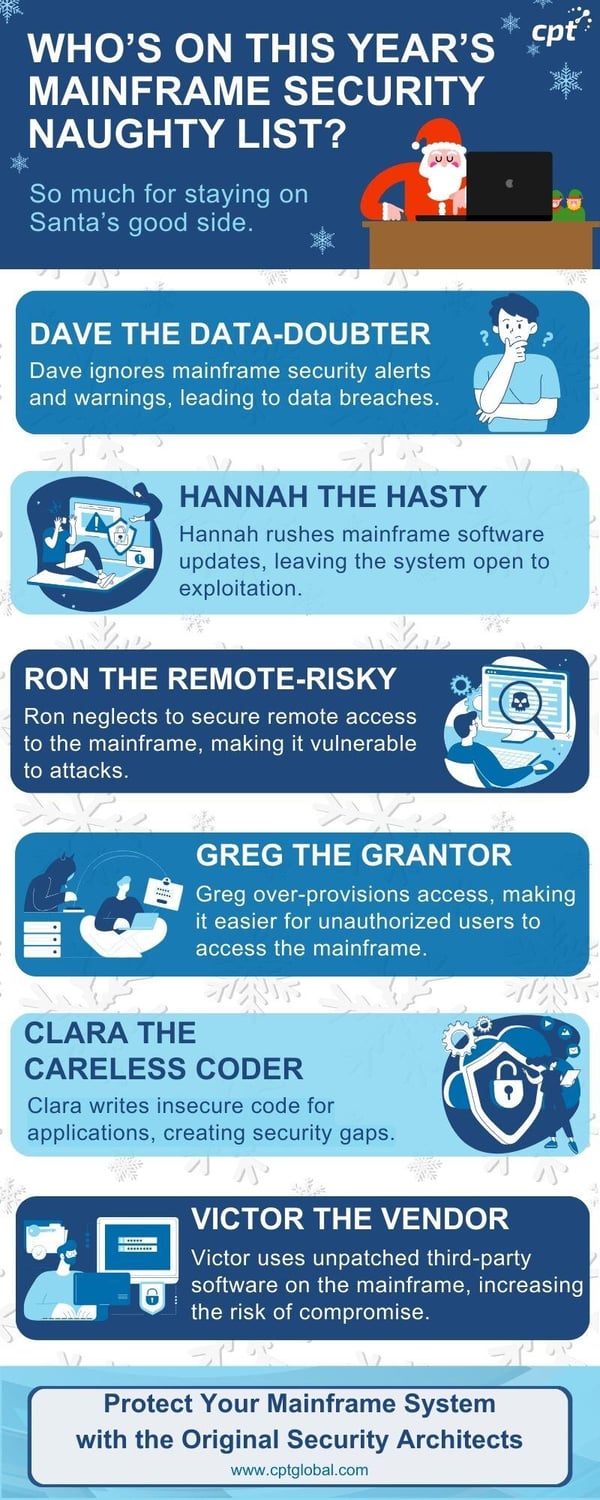
Meet the Mainframe Mischief Makers
Our infographic highlights some of the most common security slip-ups that land organizations on the "naughty list":
Dave the Data-Doubter
Dave ignores security alerts and warnings, leading to data breaches. This can happen when IT teams become desensitized to alerts, assuming they are false positives. However, ignoring these warnings can leave critical vulnerabilities open for exploitation.
For example, a recent report found that 60% of organizations experienced a data breach due to unpatched vulnerabilities.
Hannah the Hasty
Hannah rushes software updates, leaving the system vulnerable to exploitation. While timely updates are crucial for patching known vulnerabilities, rushing the process can introduce new bugs and destabilize the system, creating unintended security holes.
A study by Gartner revealed that 42% of software vulnerabilities were introduced by open source code on third-party apps.
Ron the Remote-Risky
Ron neglects to secure remote access, making the mainframe an easy target. Remote access is essential for businesses, but if not properly secured, it can provide a backdoor for attackers to gain unauthorized access.
Research from Verizon's Data Breach Investigations Report found that compromised credentials, often obtained through insecure remote access, were the most common initial attack vector in data breaches.
Greg the Grantor
Greg over-provisions access, making it easier for unauthorized users to gain entry. Granting excessive permissions to users can create unnecessary risk. Implementing the principle of least privilege, where users only have the access they need to perform their job duties, is essential for minimizing the impact of a potential breach.
A study by Forrester Research found that 80% of security breaches involve privileged accounts.
Clara the Careless Coder
Clara writes insecure code, creating security gaps. Even small coding errors can have significant security implications. Following secure coding practices and conducting thorough code reviews can help prevent vulnerabilities from being introduced into the system.
The OWASP Top 10 list consistently ranks injection flaws, insecure design, and broken access control as the most common web application security vulnerabilities, many of which are introduced through careless coding practices.
Victor the Vendor
Victor uses unpatched third-party software, increasing the risk of compromise. Third-party software often contains vulnerabilities that are unknown to the vendor or the user. Regularly updating and patching third-party software is essential for maintaining a strong security posture.
A recent study by Synopsys found that 90% of applications contain at least one open-source component, and many of these components have known vulnerabilities.
The Cost of Being Naughty
These seemingly small missteps can have major consequences, including:
- Data breaches: Exposing sensitive customer and financial information, leading to reputational damage, financial losses, and legal liabilities. The average cost of a data breach in 2023 was $9.44 million, according to IBM's Cost of a Data Breach Report.
- System downtime: Disrupting critical business operations, causing significant financial losses and impacting customer satisfaction. Gartner estimated that the average cost of an hour of IT downtime for large enterprises was $5,600 per minute - IN 2014. These costs have only gone up exponentially since then.
- Reputational damage: Losing trust and eroding customer confidence, making it difficult to recover from a security incident. A survey by Edelman found that 66% of consumers are less likely to do business with a company that has experienced a data breach.
How to Stay on Santa's (and Your Customers') Good Side
The good news is that you can take steps to strengthen your mainframe security and avoid being on the naughty list. One of the most effective ways to do this is with a comprehensive mainframe security assessment.
A security assessment will help you:
- Identify and address vulnerabilities: Proactively uncover weaknesses in your mainframe environment before they can be exploited.
- Improve your security posture: Implement effective security controls and best practices to strengthen your overall security.
- Reduce the risk of cyberattacks: Minimize the likelihood and impact of successful cyberattacks.
- Comply with industry regulations: Ensure compliance with relevant industry standards and regulations, such as PCI DSS and HIPAA.
Don't Let Security Slip-Ups Ruin Your Holidays
This holiday season, make a commitment to mainframe security. Contact CPT Global to schedule your assessment and ensure your organization stays on the nice list all year round.

Dec 16, 2024 11:15:00 AM


.png)
.png?width=500&height=500&name=Website%20Page%20Banner%20(General).png)